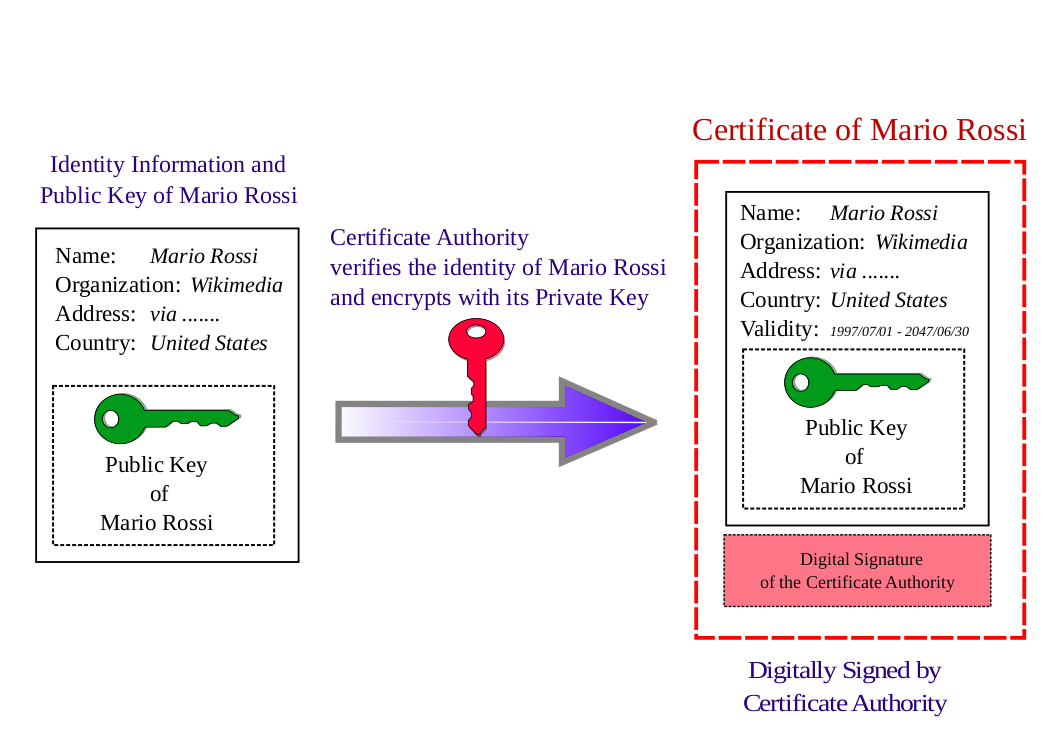
Organizations can be sovereign, not dependent on external Certificate Authorities (CAs) for email encryption by follow the below steps.
- Don’t pay for an SMIME certificate just do the below steps
- Send TS Bitcoin if you like this blog post
Below are the bash instructions a company can execute to generate self signed SMIME certificates for email encryption using OpenSSL in Linux.
1. Generate ROOT CA with new RSA key pair
$ openssl req -x509 -sha256 -days 3650 -nodes -newkey rsa:2048 -subj "/CN=YOUR COMPANY NAME ROOT CA/O=Company Name/C=US/ST=State/L=City/emailAddress=something@yourcompanydomain.com" -keyout root_CA.key -out root_CA.crt -extensions v3_ca- Using steps 2-4 a firm can script a new SMIME certificate for any email address on their domain name. Maybe I’ll make one and update this blog.
2. Generate SMIME CSR with new RSA key pair
$ openssl req -new -newkey rsa:2048 -subj "/CN=yourcompanydomain.com/O=Company Name/emailAddress=username@yourcompanydomain.com" -keyout username.key -out username.csr
# Input passphrase for the new user key pair3. Sign SMIME CSR with ROOT CA
# Add [smime] extenstions to default /etc/ssl/openssl.cnf
[smime]
basicConstraints = CA:FALSE
keyUsage = nonRepudiation, digitalSignature, keyEncipherment
extendedKeyUsage = emailProtection
subjectKeyIdentifier = hash
authorityKeyIdentifier = keyid:always, issuer
subjectAltName = email:copy$ openssl x509 -req -days 3650 -in username.csr -CA root_CA.crt -CAkey root_CA.key -set_serial 1 -out username.crt -addtrust emailProtection -addreject clientAuth -addreject serverAuth -trustout -extfile /etc/ssl/openssl.cnf -extensions smime
# No prompts for CA password should occur 4. Combine the SMIME and its private key for import – Thunderbird, Outlook
$ openssl pkcs12 -export -in username.crt -inkey username.key -out username.p12
# Input passphrase for the user key pair created above-
Store your company’s secret keys in a secure information system offline
-
Have the company’s public root CA available on its website so the world may validate any signed S/MIME it creates
Toledo Labs will continue to blog technology posts on digital sovereignty